That’s known as a ligature and they’re pretty common in many programming-oriented fonts, which usually have stylistic sets with different ligatures for different programming languages that you can optionally enable in your editor’s configuration. For example, here’s the stylistic sets the Monaspace font offers:
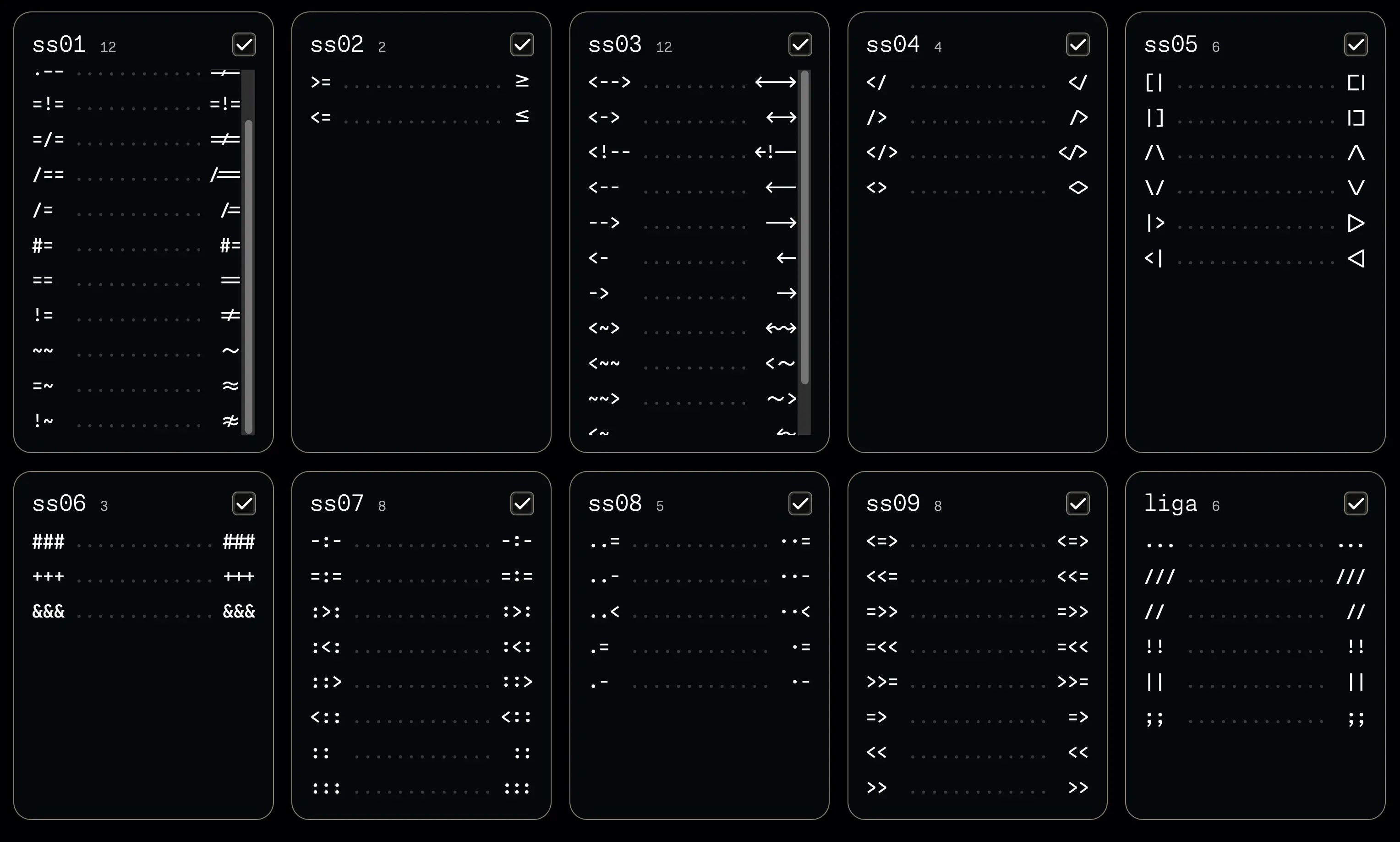
Personally I’m not too fond of ligatures so I never enable any, but many folks do like them.
Edit: and just as a side note, ligatures are super common in many fonts, you just might not notice them. Here’s some classic examples from the DejaVu Serif font, with and without a ligature:













Urr, I don’t think that’s it. I’m not sure stereo sound for vinyls has ever worked so that something like this would be necessary, and it wouldn’t really make sense – why would they have to put vocals on one channel and instruments on the other?
A stereo vinyl player just has the needle moving up and down in addition to left and right, so that the left-right axis is the sum of the waveforms of both channels and the up-down axis is the difference – which means that a regular mono player can play stereo vinyls